Hacking Satellites & Everything In-Between
Last Update:

Introduction
Disclaimer & shout-out:
Most of the stuff I learned here is thanks to Andrzej Olchawa, Lennert Wouters, François Quiquet, Angelina Tsuboi and many other people who are way more skilled than me.
If you want to check out their blogs/presentations/courses please feel free to check the references section [0]
If you like to read papers & academic research about this subject go to section [1]
If you wish to contact me or know more about my work or background, check section [2]
And keep in mind that:
This blog serves as the distilled version of the accumulated knowledge from great people.
This blog self-contained, meaning anything you might need to know is already here (unless explicitly said otherwise)
Mission, Motivation and Aim:
I’ve always wanted to write down something that is just simple enough to be accessible via the general public but also serve as a reference pillar for experienced hackers and cyber security professionals.
So I decided to make this blog.
This blog is to try and share the word of the great works in satellite security and simplify it to a general audience whilst also serving as a great reference point for veterans.
Enjoy.
Satellites, what are they?

Simple definition:
“A satellite or ‘artificial satellite’ is an object, typically a spacecraft, placed into orbit around a celestial body.(*)
They have a variety of uses, including communication relay, weather forecasting, navigation (GPS), broadcasting, scientific research, and Earth observation.
Additional military uses are reconnaissance, early warning, signals intelligence and, potentially, weapon delivery. Other satellites include the final rocket stages that place satellites in orbit and formerly useful satellites that later become defunct.”
– wiki (aka. just trust me?)
(*) : in general u can call the moon a satellite although a natural and not an artificial one…
and throughout the blog when I say ‘satellites’ I’m referring to ‘artificial-satellites’… again, just lingo…
Notice how none of this mentions the word “secure”…
And really, when you dig deeper, the only difference between your smart-fridge and that billion-dollar satellite is that your smart fridge isn’t orbiting something with the mass of 5.9722 x 10^24 kg….
Which brings us to this blog…
How vulnerable are satellites, and how can we exploit those vulnerabilities?
Spoiler Alert: Well, actually, they’re quite vulnerable (since they rely on security by obscurity)… and that’s quite astonishing considering a simple DoS attack can lead to disastrous results…
But we’ll expand on that later….
General structure of satellite systems:
First of all we need to learn and identify the different parts and terminologies related to satellites (mission control systems, ground stations etc..)
Now, we can more or less agree on the general structure of a satellite system..
and they can be roughly summed up in this visual:
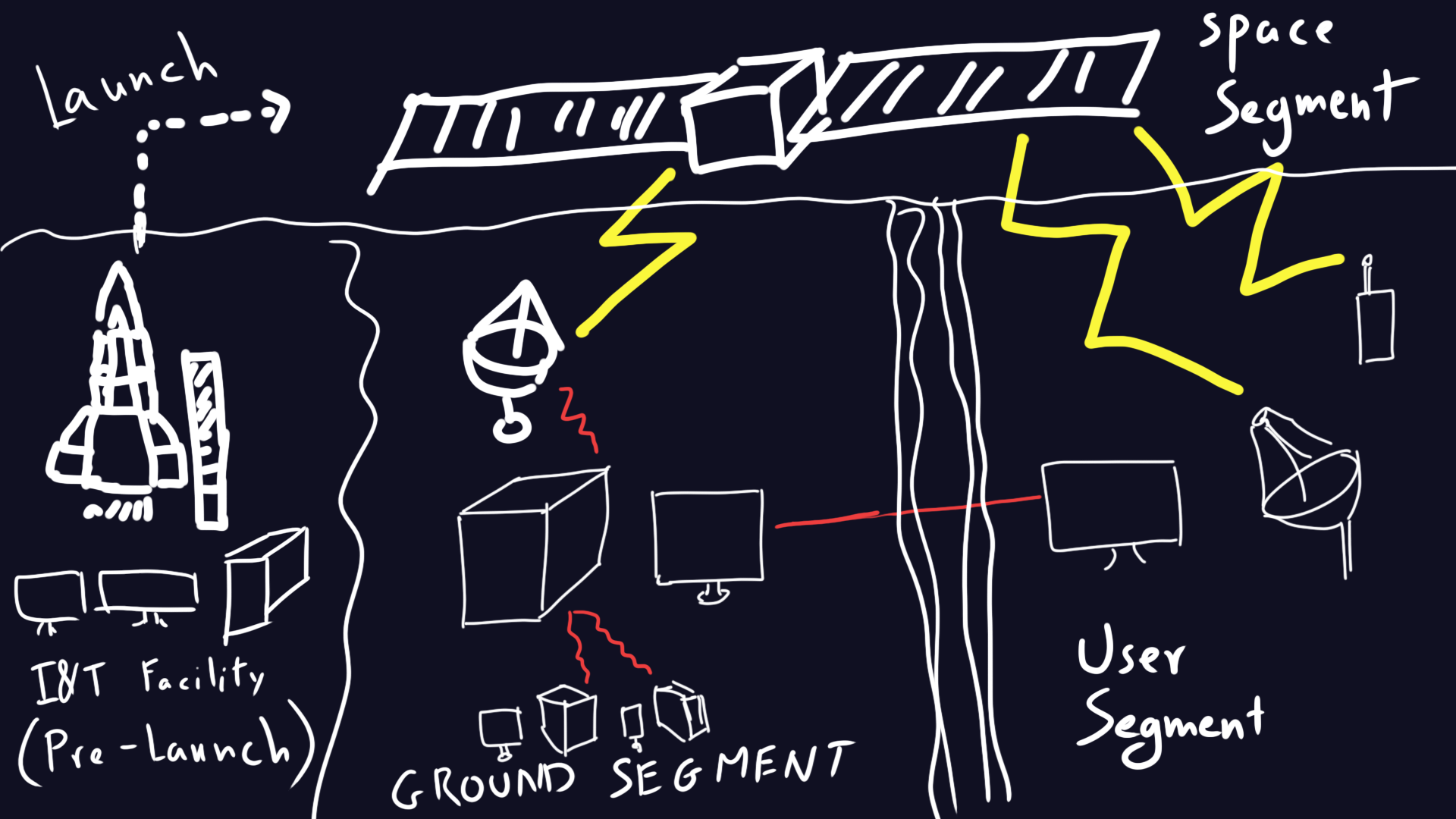
(red ‘lines’ means your usual communication protocols like IPv4/6 and whatnot.. while yellow ‘lines’ means other protocols)
which is composed of:
Space Segment (Satellite)
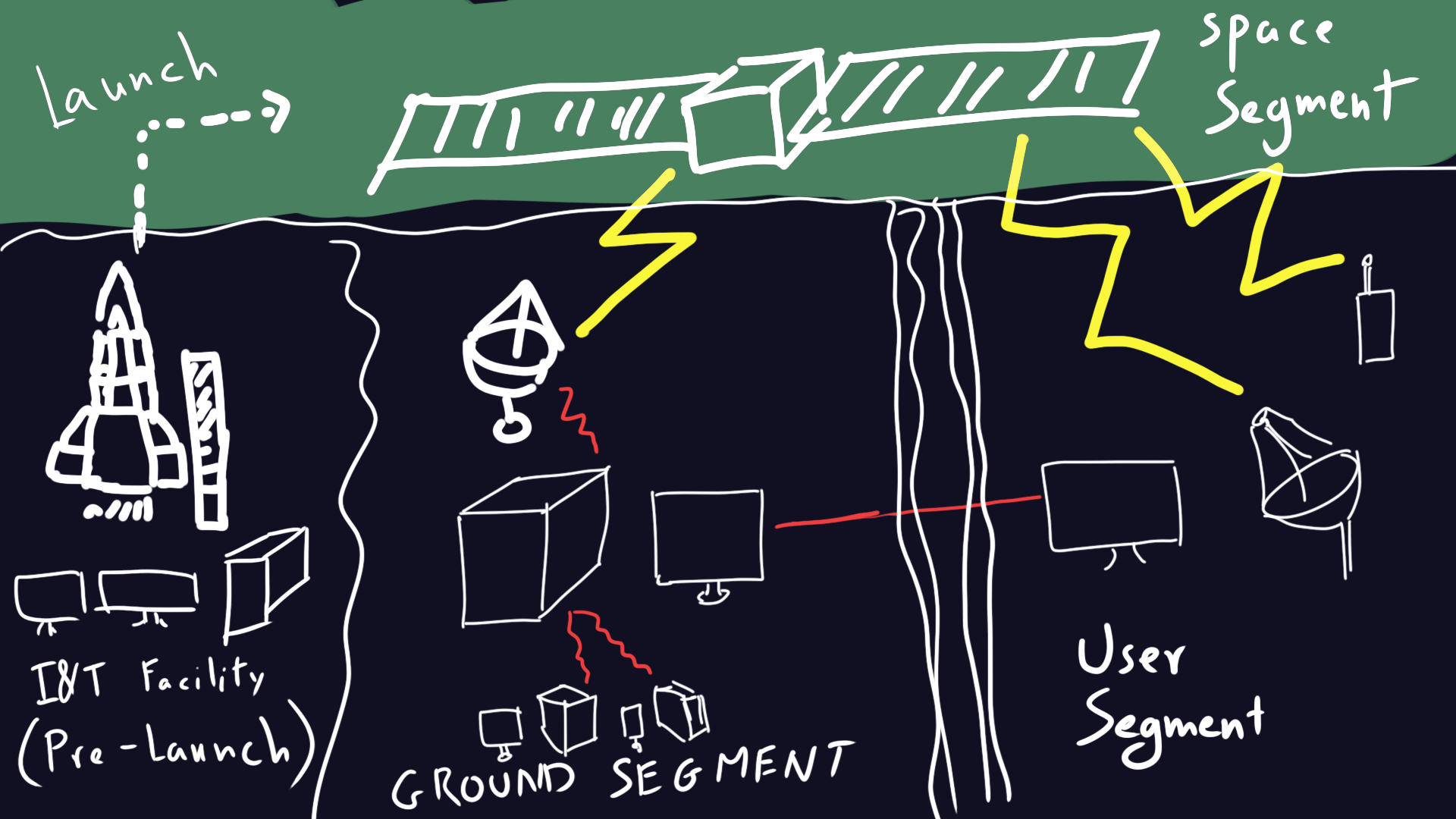
This includes the satellite itself and its onboard systems:
- Payload – The primary mission equipment (e.g., communication transponders, cameras, scientific instruments).
- Bus (Platform) – The supporting structure and subsystems, including:
- Power System – Solar panels and batteries to generate and store energy.
- Thermal Control System – Regulates temperature in space.
- Attitude and Orbit Control System (AOCS) – Maintains the satellite’s orientation and orbit using thrusters and reaction wheels.
- Telemetry, Tracking, and Command (TT&C) System – Enables communication with the ground station for control and data transmission.
- Propulsion System – Adjusts the satellite’s position and orbit.
etc…
If you’re looking for a great video that explains how to build a satellite you can check The Efficient Engineer’s video (just know that this video goes really in depth in everything satellite related, and we’re merely interested in the security side of things which is roughly around 15:54 which covers the telemetry & communication part):
There’s also Mark Rober’s video for the very curious:
Now, hacking the satellites themselves has a different approach than say hacking the other parts like ground or user segments…
They’re like hacking embedded systems but think different protocols and whatnot…
And I’ll try to cover different attack vectors and their impact shortly after detailing the aforementioned segments…
Note: If you wish to experiment with building satellites yourself, there is actually a cool site called hack-a-sat Moonlighter that allows you to build a cubesat and experiment with it!
and if you wish to learn more about satellites and hack-a-sat in general you can do so at hackasat.com/learn
Ground Segment (Ground Stations)
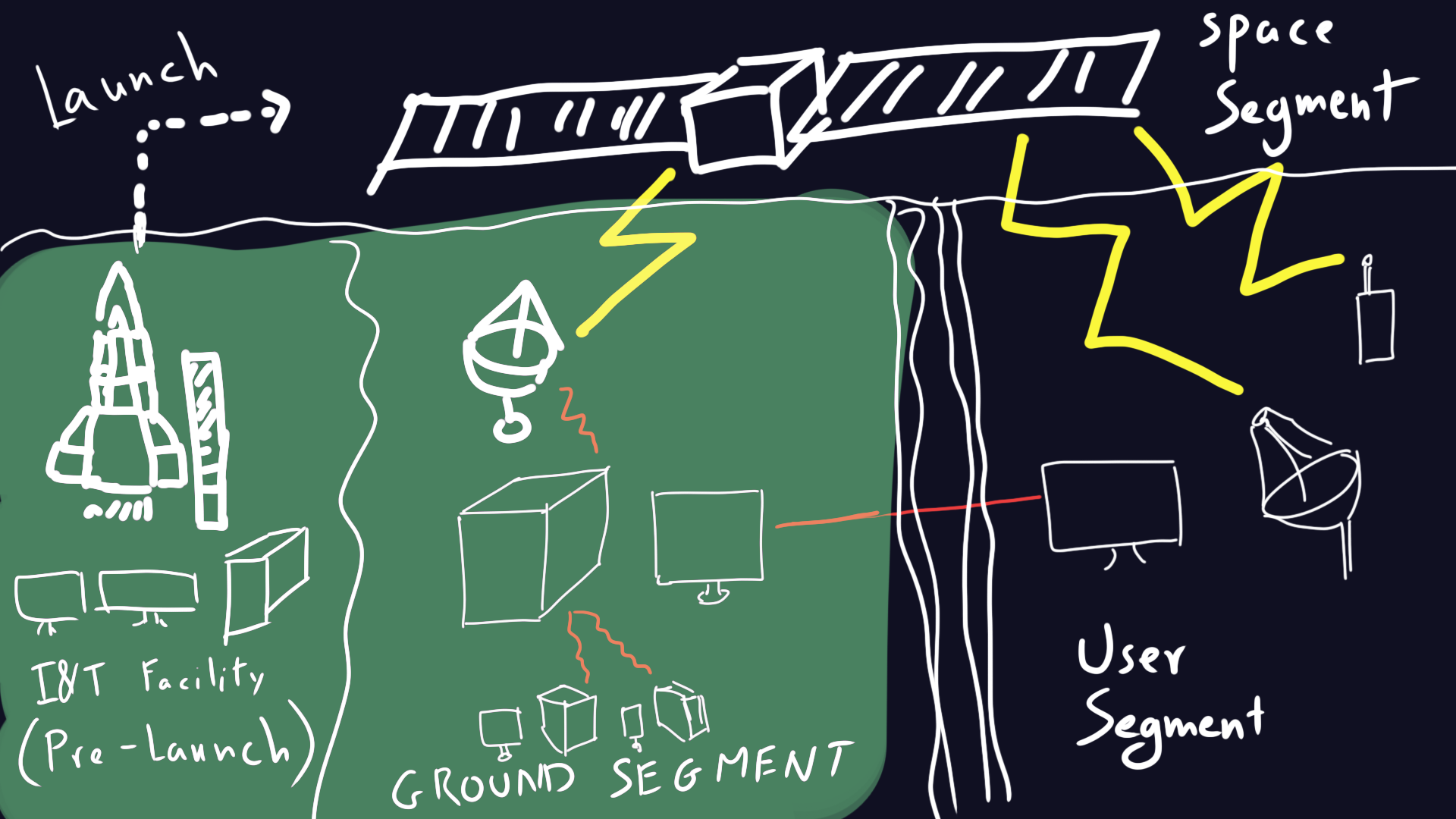
The infrastructure on Earth that communicates with the satellite:
- Ground Control Station – Monitors, controls, and manages the satellite’s functions.
- Tracking and Telemetry Stations – Receive and process signals from the satellite.
- Mission Control Center – Manages operations, data processing, and mission planning.
so think your usual enterprise and your usual devices… servers, routers etc…
Basically hacking this segment is akin to hacking any good-ol’ company..
Just keep in mind that a lot of attack vectors and hacking incidents happen here…
User Segment
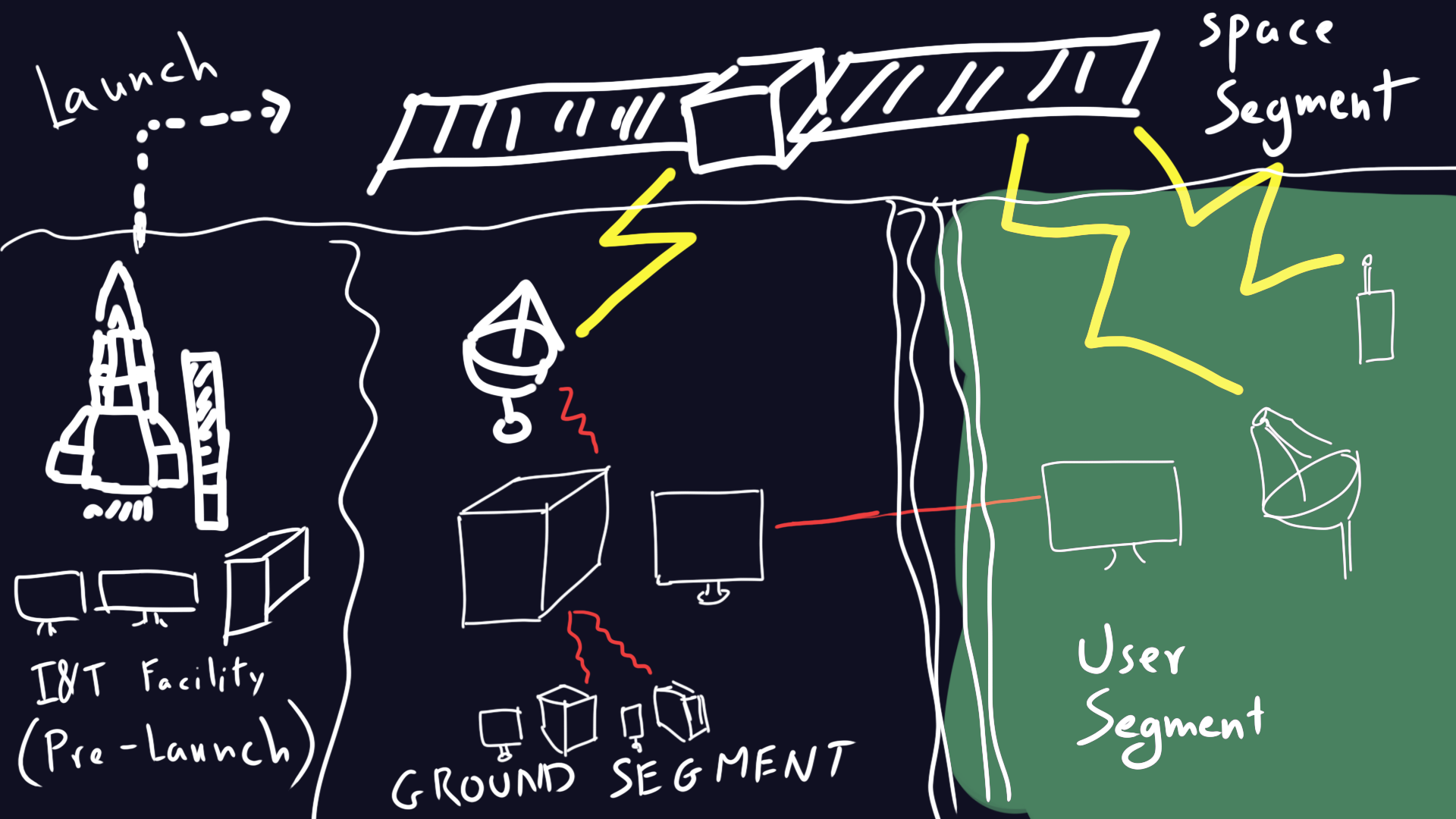
The end-users and devices that utilize satellite services:
- Receivers (Antennas, Dishes, Terminals) – Used by individuals, businesses, and governments to receive satellite data.
- Mobile Devices and GPS Units – Utilize satellite signals for navigation and communication.
- Broadcast and Communication Networks – Television, internet, and telecommunication services relying on satellite signals.
and these can range from your old civilian antennas and dishes to military ones…
(“bunker” from Nier Automata)
Note:
It might sound bizarre to go after the user segment seeing you’d have to hack user dishes, routers and antennas… It’s like saying “hack every person who has X app installed on their phone”..
But impact wise, It makes total sense since if you want to cut down communications (say for a rival opponent) you really don’t care in which segment It happens and usually the user segment seems to be the easiest to tamper with…
And since It happens to be the easiest segment to attack, It allows for the absolute shutdown of critical infrastructures, communication and GPS services etc…
Pair this with nation-sponsored hackers who have to do that for a living, you find that a lot of attacks happened in this segment simply because military bases go hand-in-hand with this kind of attack…
tl;dr: This is where most hacks actually happen, and I’ll mention a few examples.
ENOUGH TALK! – LET’S START HACKING!

Now hacking space satellites is quite sophisticated and is usually done by very experienced people (I know, shocker right?)…
But It’s not rocket science… kinda?
Whilst researching this I found all kinds of crazy vulnerabilities and exploits documented by some brilliant researchers, some of which were only theoretical and thankfully the companies/agencies running those satellite systems were able to fix those issues.. whilst others were exploited in the wild!
Some of the hacks are not disclosed publicly (for one reason or the other)…
which makes collecting samples for this blog quite annoying…
But thankfully I was able to gather a few theoretical attacks (ones that were implemented by vendors themselves / researchers) and others practical and well documented like the Viasat attack…
Hacking OPS-SAT
Now, I was hesitant on choosing which hack to cover first…
But then I decided to go with hacks around OPS-SAT… mainly because It’s apparently the “First in-orbit research platform for space cybersecurity” and because It has a lot of public research and blogs about it…
There is also the fact that Olafur Waage was able to run DOOM on it making it the “First satellite to run DOOM in space”!!
anyways…
For those who don’t want to dive deep into OPS-SAT
We can just summarize like this:
- Satellites are computers in space.
AND
- Servers are just computers.
And the cloud is just servers that you have access to.
so basically, the cloud is just computers.
Someone looked at the former thought of taking the “cloud” one step further…
and now we have
CLOUD IN SPACE!
or what is now called
“Sattelite-as-a-servivce (or SATAAS for short)”
And It’s useful…
In our case (OPS-SAT): It’s for real-time data analysis of earth and earth’s orbit…
Other relevant links for OPS-SAT:
Automation of Operation and Testing for European Space Agency’s OPS-SAT Mission - Felix Hessinger
Hacking the Stars: A Fuzzing Based Security Assessment of CubeSat Firmware - Florian Göhler
ESA & THALES (THALIUM)
THALES (Group) along with ESA (European Space Agency) achieved the first (published) worldwide hacking demo of an in-orbit satellite!
(Hence why I decided to start with this attack vector)
Now, even though It took cooperation from both THALES and ESA (two big names in the industry by the way), It still took considerable effort to hack the satellite, which makes one wonder if a black box approach is even possible..
As far as I know, there’s no published source code or firmware for me to analyze…
So “show me the code” doesn’t work here and all I can do is speculate..
And honestly I don’t think I can say anything that François Quiquet hasn’t said already in his blogs:
- Thales seizes control of ESA demonstration satellite in first cybersecurity exercise of its kind
- Hacking demo at CYSAT 2023: world first or “déjà vu”
- Thales demo at CYSAT: what was the point again
But if you wish to dig deeper into the attack and the cooperation in general, they presented it at CYSAT which is one of the biggest european events tailored towards cybersecurity for satellites and the space industry in general:
If you wish to read a blog that covers the attack chain in a more technical matter (although still limited to what we can gather from the slides) you can read Hacking an On-Orbit Satellite: An Analysis of the CYSAT 2023 Demo by The Aerospace Corporation
But to summarize it in simple words, this attack vector by THALES assumes you have already hacked the ground station and was able to do a java deserialization attack…
Really, It’s that simple…
I mean, when you look back at it after crossing every failed attempt and trying every possible attack vector and navigating every possible path It looks a bit simple… But It is nothing short of a technical achievement only possible through high levels of dedication.
THE DESTRUCTION OF THE LOW EARTH ORBIT SATELLITES’ SYSTEM

Well, the title and .gif image taken from Stellaris might be a bit exaggerated…
But there is actually a high chance of a malicious actor (hypothetically) doing this…
You can check this Master’s Thesis by Matteo Calabrese called “Space Oddity: Space Cybersecurity Lessons from a Simulated OPS-SAT Attack” which roughly covers the general structure of this attack…
And if you want a video explaining this attack vector you can watch Matteo Calabrese‘s demo about it (presented at CYSAT 2023):
I will get just a tiny bit technical here since mentioning the thesis paper is boring without having code alongside it…
But the gist of it is simple:
Exploit a dylib (dynamic library) hijacking(*) attack on valid software; to inject malicious code and allow the attacker to sabotage the mission and effectively spoof the satellite’s payload.
(*): if you wish to learn more about dylib hijacking you can check this presentation by Patrick Wardle - DEF CON 23 - DLL Hijacking on OS X (mirror on TIB AV-Portal)
which is really simple once you ignore the whole hacking jargon…
The conditions are:
- You have code/software/application (whatever you wanna call it), that references (uses/calls etc..) another part of code conventionally named linked libraries (in windows they’re called DLLs, in linux they’re those ___.so files etc…)
- You have access (writing access) to that linked library.
BOOM
Now when you modify the linked library (or replace it really) you also modify the original code’s behavior.
quite simple <3
And how would we do that here?
The thesis mention one interesting scenario:
First we check for interesting applications that are hosted on OPS-SAT (OPS-SAT allows user code upload by design)
A cool one being Georges Labrèche‘s project, the opssat-smartcam (the first use of deep convolutional neural networks (CNN) on-board a spacecraft) which makes a syscall to an interesting binary called "ims100_testapp" that does the image acquisition for the CNN..
You can check the exact function that does this call at line 899 and 910
1 | |
Well, first we check for linked libraries with ldd:
(The results are taken from the mentioned thesis)
1 | |
Then we use a tool called fakelib.sh by Eduardo Blázquez and assign the appropriate gcc compiler for this architecture to create the malicious linked library…
At this point the attack is clear…
And can be roughly summarized in this image:
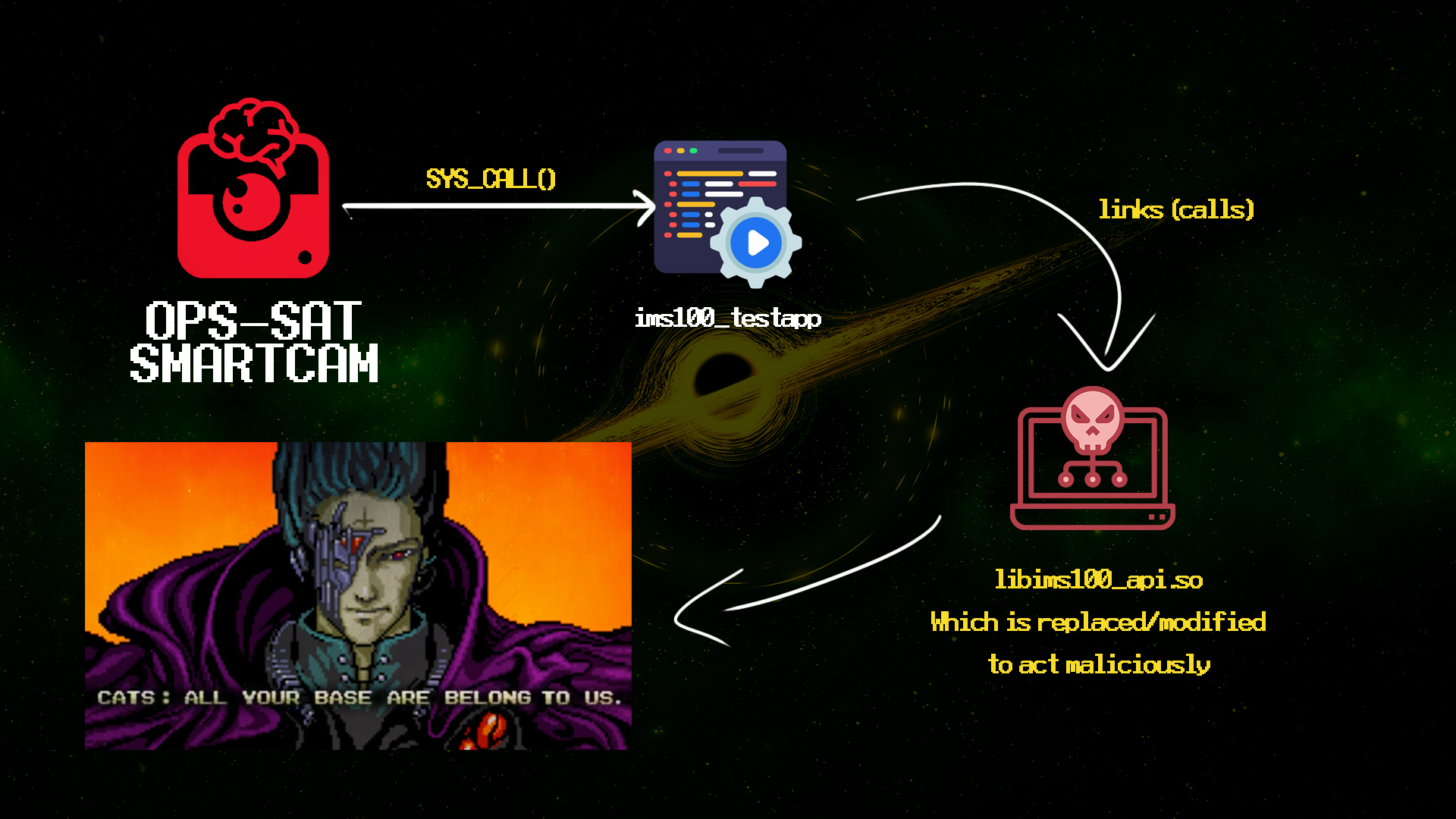
All is left is persistence and lateral movement (aka. taking FULL CONTROL of the system)
I’ll skip the tedious details of the simulation itself and you can check the thesis if you want more details but just know that without actual open source distribution of OPS-SAT’s Satellite Experimental Processing Platform (SEPP)… A lot of the stuff here is either theoretical or missing…
The best I can do here is try and replicate a dual twin of what I “think” is OPS-SAT’s actual software from what I can gather online…
So I’ll just take the author’s opinion here:
[…] Malicious activities like exploit execution and lateral movement might not be actively detected, unless they produce noticeable side effects. If a more sophisticated attack, involving exploits for both the payload and the bus system, were to be developed, it would be interesting to assess whether the spacecraft’s recoverability could be undermined and entirely compromised. [4.3. DEVELOPING THE ATTACK P51]
and
In a realistic scenario, the attacker could penetrate the OBC and take control by modifying cryptographic material or isolating communication interfaces, effectively locking out the ground segment. This would place the entire satellite under the attacker’s control, enabling various other scenarios included in the SPARTA matrix, such as destruction, denial, disruption, and degradation. [4.4. VISUALISING THE ATTACK P53]
which, with vivid imagination, one can imagine the following scenario:
𝐖𝐡𝐚𝐭 𝐢𝐟 𝐭𝐡𝐞 𝐛𝐢𝐧𝐚𝐫𝐲 𝐢𝐧 𝐪𝐮𝐞𝐬𝐭𝐢𝐨𝐧 𝐰𝐚𝐬𝐧’𝐭 𝐭𝐡𝐚𝐭 𝐨𝐟 𝐭𝐡𝐞 𝐜𝐚𝐦𝐞𝐫𝐚 𝐛𝐮𝐭 𝐢𝐧𝐬𝐭𝐞𝐚𝐝 𝐭𝐡𝐞 𝐨𝐧𝐞 c𝐨𝐧𝐭𝐫𝐨𝐥𝐥𝐢𝐧𝐠 𝐭𝐡𝐞 𝐬𝐚𝐭𝐞𝐥𝐥𝐢𝐭𝐞’𝐬 𝐩𝐨𝐬𝐢𝐭𝐢𝐨𝐧?
or as said in the thesis:
One alarming possibility is that an attacker gains advanced capabilities, like compromising the bus system, using it to take over the entire satellite. In such a scenario, the satellite could be directed towards other spacecrafts, transforming it into an anti-satellite weapon. [5.1. DISCUSSION 59]
Oh…
(taken from Gravity 2013)
Disasterous results will happen…
Disasterous results indeed…
Here, we’re interested in the GNC:
GNC (Guidance, Navigation and Control System): The system responsible for guiding and controlling the spacecraft’s movements, maintaining its orientation, and ensuring accurate positioning (e.g, in orbit). [2. BACKGROUND P6]
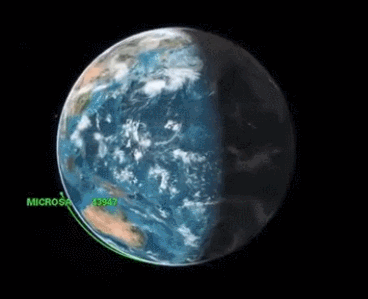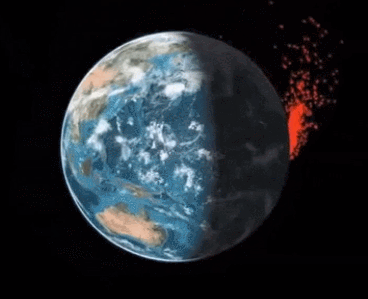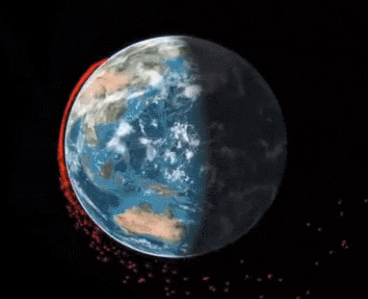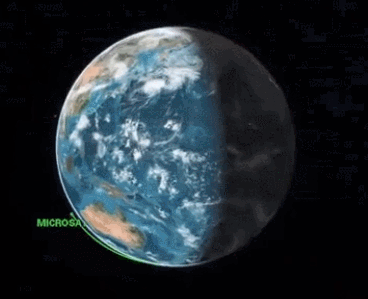
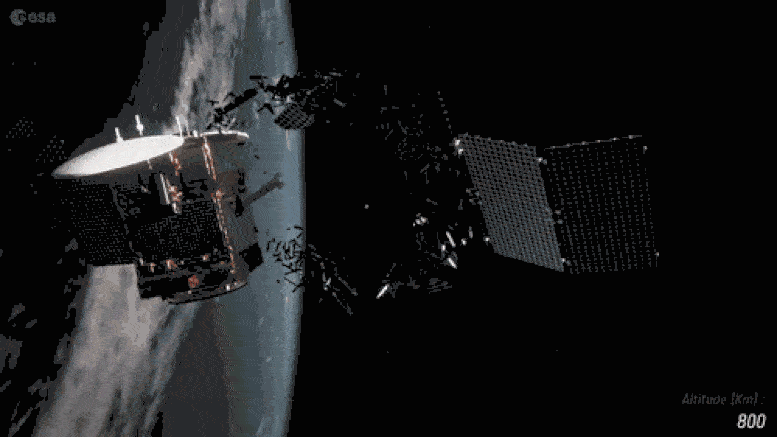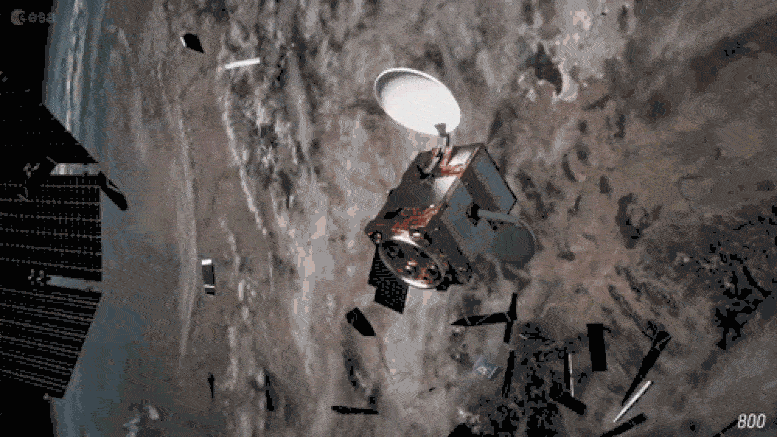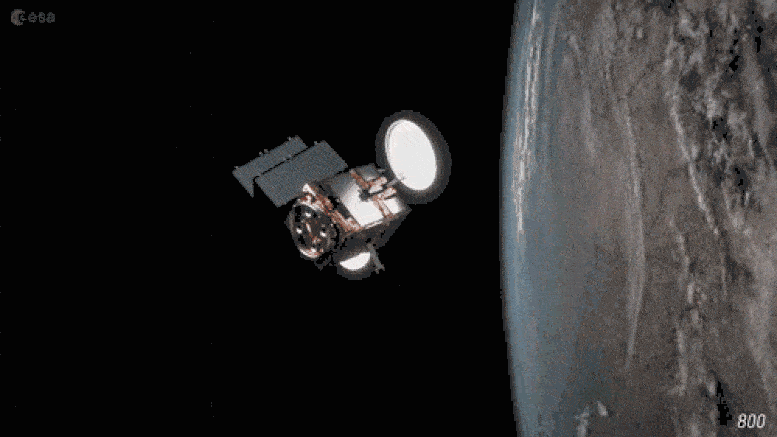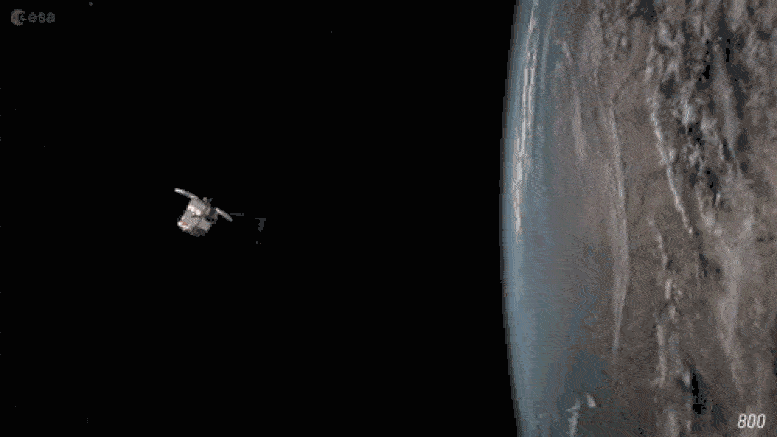
Taking control of it and aiming it towards other satellites and spacecrafts would create what’s known as the Kessler effect where you’d have a domino effect of satellites destroying eachother and rendering the whole LEO system useless (don’t worry, MEO and GEO are probably safe)
And I love this quote from the wiki page on the Kessler effect:
Any intelligent civilization which becomes spacefaring could eventually extinguish any safe orbits via Kessler syndrome, trapping itself within its home planet.[29] Such a result could happen even with robust space pollution controls, as
a lone malicious actor on a planet could cause a Kessler syndrome scenario.[30] Humanity could be on the path to a similar fate, soon to trap itself on Earth with no future as a spacefaring civilization.[31]
(relevant sources):
[29]: Forgan, Duncan H. (2019). Solving Fermi’s Paradox. Cambridge Astrobiology. Cambridge University Press. doi:10.1017/9781316681510. ISBN 978-1-316-68151-0. OCLC 1098275130. OL 21201773W.
[30]: Hamilton, Chase (2022). “Space and existential risk: The need for global coordination and caution in space development”. Duke Law & Technology Review. 21: 1–60.
[31]: Kessler, Donald (1971). “Estimate of Particle Densities and Collision Danger for Spacecraft Moving Through the Asteroid Belt”. Physical Studies of Minor Planets. 267. NASA SP-267: 595–605. Bibcode:1971NASSP.267..595K.
Swirling Fragments of Past Space Endeavors: Threatening Our Future in Space
ICARUS Simulation (2021)
This part covers the theoretical attack which was simulated and studied thoroughly
by the authors of the paper ICARUS: Attacking low Earth orbit satellite networks:
Giacomo Giuliari, Tommaso Ciussani, Adrian Perrig, and Ankit Singla, ETH Zurich.
which you can check here
Now, I actually found out about ICARUS from another paper called “SoK: Evaluating the Security of Satellite Systems” which goes more in depth about possible attack vectors and different attacks on different segments, so check it out.
And the ICARUS attack is quite “simple” security wise:
It’s a DDoS attack on LEO (Low Earth Orbit) satellites, and in their terms “exploiting their decentralized structures to flood targets with excessive traffic and cause service disruptions.”
So in cybersecurity terms, even a skid can do this…
It’s so simple in fact you can pretty much sammarize it in this image:
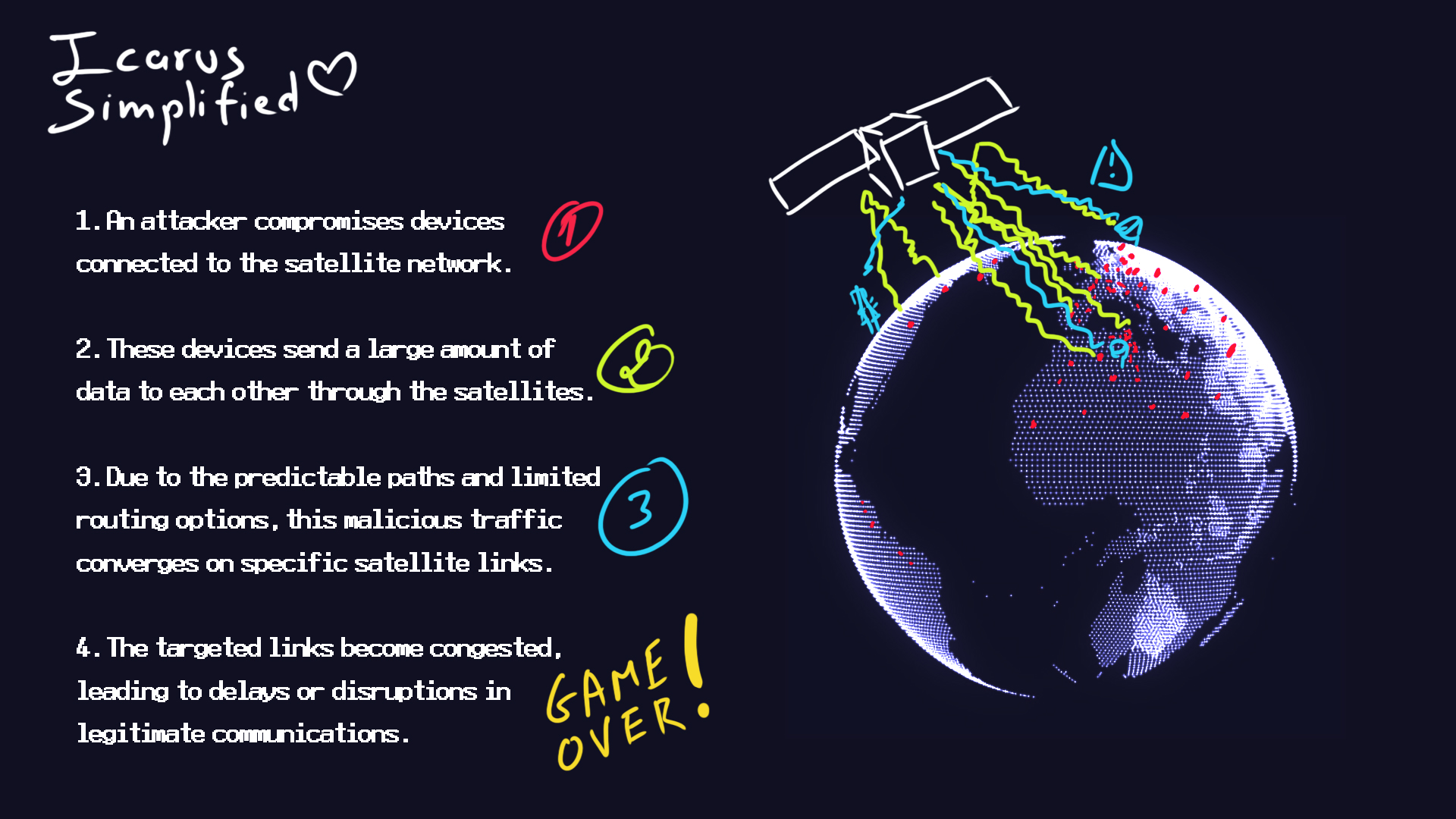
And this mainly relies on the fact that a satellite’s position has to be known by everyone at all times… which is really the main challenge facing say, internet satellites, like starlink…
There’s also the fact that this targets the satellite segment…
(It’s always fun when you have those :^) )
So the issue here can’t just simply “fixed” with a firmware update on the fly… It has to be taken in consideration pre-launch when designing the satellites’ network…
And It’s not an avoidable risk either because not doing so would just result in the non-availability of your service and pretty much wasting thousands if not millions of dollars on satellites that can only be considered by then nothing but a useless pile of expensive trash orbiting earth…
So let’s hope these theoretical studies are well researched and analyzed before launching anything into orbit.
You can watch the authors’ video on it:
The paper can also be found here
and there’s a github repo for those who want to reproduce the simulation:
Github Link
And really that’s pretty much it… dunno how much I more I can add to a DDoS attack…
I guess the name is cool? ICARUS… And knowing how geeky hackers get, It’s likely a Deus Ex reference <3
Hacking Starlink with 25$ and a cup of coffee
Actually the cup of coffee is optional…
There is a lot to Starlink: routers, user terminals, ground stations and space stations etc…
And if you’re interested more on how this whole Starlink Internet works you can watch this video
Although It’s VERY optional…
And there’s a lot of parts here that interconnect and a lot of researchers who have independently researched Starlink and contributed to making it more secure.
One of the most interesting hackers I found was MikeOnSpace (couldn’t find any twitter(X)/bluesky socials so thought I’d mention his YT channel…) in his playlist where he goes in depth into tearing down Starlink’s satellite dishes and reversing their firmware (there’s also this unlisted video by Ken Keiter where he explains the different parts that make the dishes and elaborates on the design choices)…
There is also research by COSIC: Dumping and extracting the SpaceX Starlink User Terminal firmware and here you’d find various firmware dumps and how to get root access to user terminals by unfusing them.
Interestingly, there is research by Quarkslab: Diving into Starlink’s User Terminal Firmware
and they even published a few tools you can use to reverse the firmware on Github (quarkslab/starlink-tools)
(Both of these firmware dumps have been discussed on Hacker News by the way: link_1(COSIC) link_2(Quarkslab))
And some have even gone ahead and reversed each starlink router starting from gen_1 like Oleg Kutkov:
Analysis and reverse-engineering of the original Starlink router
Initial analysis of the Starlink router gen2
Starlink rev 3 (V2) power architecture
But, the most interesting research by far (and the main hack in this part) is done by Lennert Wouters.
It can be roughly summarized in this 1 minute video by Low Level:
and for the technical people out there:
The hack consists of exploiting a voltage fault injection to cause the firmware signature verification to fail leading to a root terminal.
Anyone non-technical reading that would think It’s just a quote taken from a sci-fi movie…
But for my tech-savvy hackers out there, you can watch the legend‘s presentation about it from DEF CON / Blackhat (he presented at both and they’re not so different from eachother):
You can also find the relevant slides here: “blackhat: Glitched On Earth by Lennert Wouters”
SPACE WARS & The Viasat Attack (2022)
Now, the Viasat attack is probably one of the most documented events when It comes to cyberattacks aimed at satellites.
To summarize it:
The Viasat hack was a cyberattack against the satellite internet system of American communications company Viasat which affected their KA-SAT network.
Now I’m not pointing fingers who did it… But the NSA claims It was Russia, so…
…
Yeah It was Russia… In fact the attack happened on the day of Russia’s invasion of Ukraine..
So most likely It was a planned attack that was only executed either because a convenient opening was found or an order was given…
Whichever It is, the fact is that this is probably the most sophisticated and most coordinated attack on satellite systems that has been studied and analysed publicly.
But if you want a deeper analysis on the whole Russia-Ukraine cyberwar please check out Hacking the Cosmos: Cyber operations against the space sector: A case study from the war in Ukraine by Clémence Poirier where she dives into the different attacks that happened, relevant threat actors, their behaviors and what It means as a whole to the european space sector and critical infrastructure in general.

However, we’re interested in the technical aspect of the attack and not the geo-political aspect of it…
which can be explained in this sentence:
A VPN installation, in a Turin management center, which provided network access to administrators and operators was targeted and the hackers gained access to management servers that gave them access to information about company’s modems. After a few hours, the hackers gained access to another server that delivered software updates to the modems which allowed them to deliver the wiper malware AcidRain.
So basically a wiper attack that happened like this:
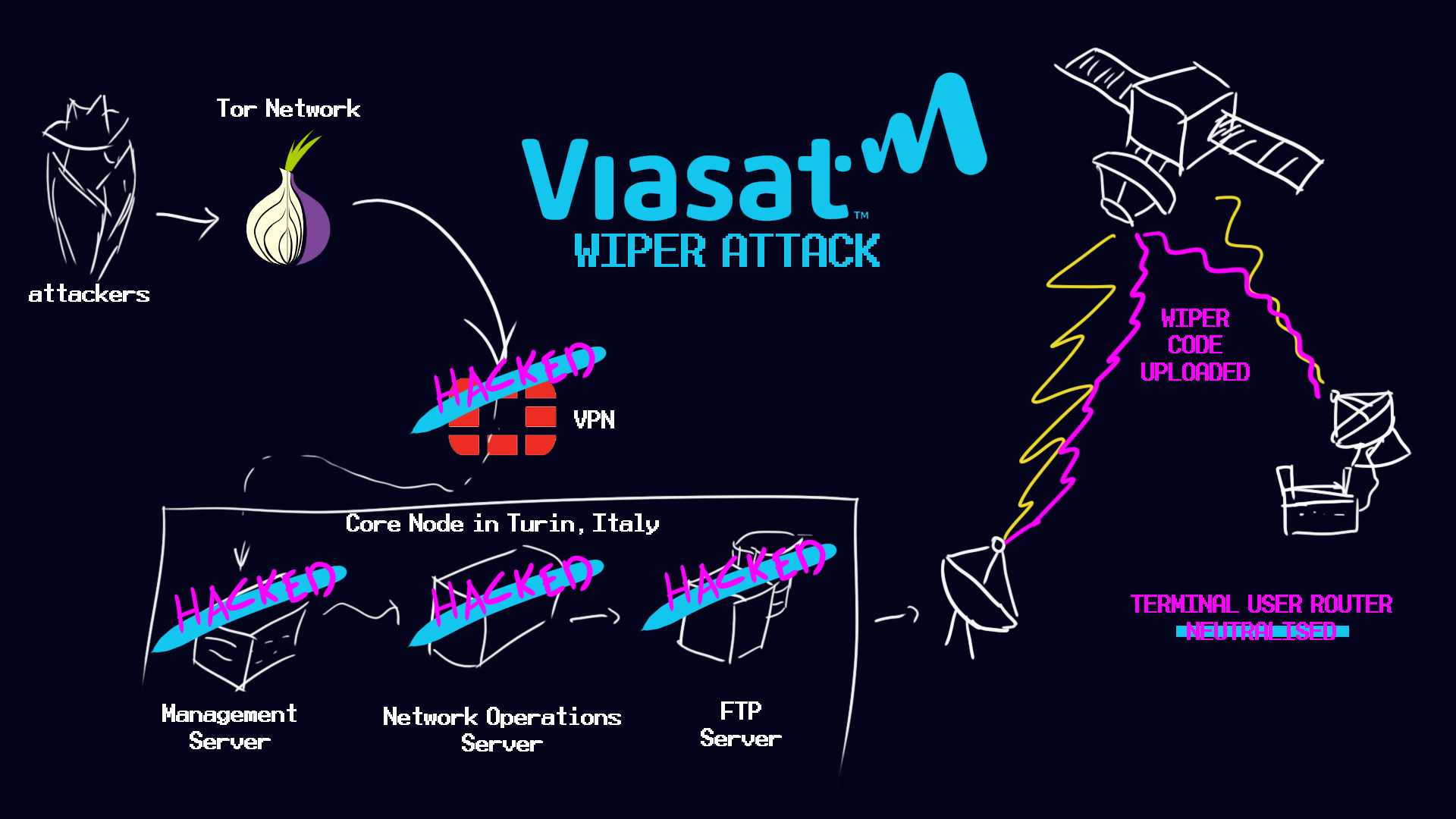
and results?
Thousands of Viasat modems went offline. The attack caused the malfunction in the remote control of 5,800 Enercon wind turbines in Germany and disruptions to thousands of organizations across Europe…
Multiple government agencies got involved all of which were contacting Viasat to no avail…
You also need to understand that the affected routers were permanently damaged… meaning there was no update and literally nothing Viasat can do to repair the damages other than replacing the routers themselves…
And so, the Viasat incident response team was made on the fly and they tried to dynamically adapt to the different attacks that were happening and thoroughly analysing the wiper attack.
(Note: there were also other attacks like a DHCP relay attack which was mentioned around 35 minutes into the video)
If you want to learn more about what Viasat learned from this attack, the investigation and digital forensics done by the NSA and the logistical and criminal side of things, you can watch this talk:
VSAT HACKING - One Man Army
(Footage Taken From Dead Space)
Can a singular malicious bad actor hack VSAT (Very-small-aperture terminal) modems on his own?
Can a hacker with 2000$ worth of equipment and advanced knowledge in this field cause chaos and disruption?
The answer is an astonishing YES!!!
You can hack VSAT modems SOLO!
Without access to any ground station or any specialized equipment…
I don’t know how this went under the radar, but there is this paper that showcases how you can wirelessly attack VSAT satellite routers (modems)…
And yes, WIRELESSLY! As in someone aiming a random dish at your satellite router and Voila! You’re hacked…
And “hacked” here ranges from:
- resetting the modem
- updating the modem and uploading a malicious firmware
- Obtaining a remote admin shell!!! YES! Over-the-air based RCE!
The first mention of this attack is availabe at Wireless Signal Injection Attacks on VSAT Satellite Modems @USENIX where It was researched and published by Robin Bisping, Johannes Willbold, Martin Strohmeier and Vincent Lenders.
You can read the Wireless Signal Injection Attacks on VSAT Satellite Modems Paper here
Which is provided alongside a video explaining it (although I advice watching the DEF CON presentation mentioned later instead):
BREAKING THE BEAM
The attack was also presented at DEF CON by the mentioned authors titled "Breaking the Beam: Exploiting VSAT Satellite Modems from the Earth's Surface" and thankfully they’ve shared all the relevant slides.
They go even more in depth in their presentation at DEF CON:
And honestly this defcon presentation uncovers a lot of the things they didn’t cover in that paper.
Note: relevant info about the DEF CON presentation can be found here: defcon_32_speakers#54510
Now, as to my knowledge, there’s no public CVE for this hack but the authors have already contacted the security team of the providers so hopefully they’ve already fixed this issue…
The attack targets Newtec MDM2200 Satellite Modems which have already reached their EOL (end-of-life) where you’d usually be prompted with This product has reached end of life and has been replaced by the MDM2210 series but you’d still find it being used today.
And honestly the main part that caught my attention here was the RCE so I’m going to dig deeper on how It’s implemented:
First, great conditions were met (from an attacker’s perspective):
The router uses an
outdated Operating System,
to be precise It’s linux version (2.6.35) (Linux_2_6_35) which
was released on the 1st of August, 2010.
Yes, 2010! For reference,
that’s roughly when most people used windows XP
and everyone was listening to Hatsune Miku‘s
baka baka baka (Triple Baka)!!!A Buffer Overflow (BOF) vulnerability exists within the code
and thanfully we can have an idea of how that looks like insw_download(binary included in the modem that handles updates):
1 | |
(Explanation: sscanf() here has no upper limit to the bytes It reads from “buf” which means we can supply it with the 80 needed for “vuln” and start overwriting values, variables and registers that come after it…)
It also listens to a multicast range (from the slides the application is listening to 239.1.0.1)
So in conclusion, It can be easily hacked, or rather, pwn‘ed with only a few scripts or by using pwntools and the exploit itself (the ROP chain) can be more or less like this:
1 | |
And this would allow for the injection of our custom script (in our case here system(“/bin/sh”)).
Now simply sit down, aim your antenna and have a nc listener on the side, and that’s it…
The only change we might apply here is the way our terminal communicates with that of the modem; but seeing how It uses TCP(&UDP)/IP for Its Transport and Network layer on top of DVB-S2, there’s really not much difference from your usual network communication…
Other fun stuff!!!

𝐃𝐎 𝐍𝐎𝐓 𝐑𝐄𝐏𝐋𝐈𝐂𝐀𝐓𝐄 𝐓𝐇𝐄𝐌
Or at least if you do, I'm in no way shape or form associated with what you do <3
Creative ways to get arrested, ADS-B/C & SDR (Software Defined Radio)
If you’re interested in learning more about software defined radio
do yourself a favor and watch this presentation by Gerard de Jong:
Here we’re more interested in the ADS-B part mentioned around (28:28)
And my main point with this part here is that
systems used for mission-critical automatic and human decisions, and have direct impact on the overall air-traffic safety suffer from:
- lack of entity authentication to protect against message
injection from unauthorized entities. - lack of message signatures or authentication codes to
protect against tampering of messages or impersonating
aircrafts. - lack of message encryption to protect against eavesdropping.
- lack of challenge-response mechanisms to protect
against replay attacks. - lack of ephemeral identifiers to protect against privacy
tracking attacks.
In fact, most of this is unfiltered and accessible to everyone…
Meaning any enthusiast, researcher and journalist can easily track his flight (or any flight for that matter) at globe.adsbexchange.com/
Just imagine someone creating artificial “ghost” planes and all of them are calling a 7700 emergency…
In fact, by using a Raspberry Pi you can pretty much spoof on all ADS-B traffic, Angelina Tusboi goes in depth into this in this DEF CON presentation:
And you can check this paper: Ghost in the Air(Traffic): On insecurity of ADS-B protocol and practical attacks on ADS-B devices that goes more in depth into ADS-B and how it can be exploited.
(It also references my favorite movie & show Ghost In The Shell <3)
You can check references for more papers/research on SDR and ADS-B security by the way…
Note: There’s also “ADS-C” that has been on the rise lately and there is a great presentation about it by Martin Strohmeier
Free Internet / Phone calls:
If you wish to go back in time and experience high latency internet connections that you’re pirating from a foreign satellite, then I suggest you watch Peter Fairlie‘s video about it:
Hacking dead satellites & jamming broadcast signals
Just thought I’d leave this part here to say that other types of satellite hacking exists…
mainly hacking in the sense of managing broadcast signals or interfering with dead satellites…
This video presentation (from DEF CON 30) showcases how a hacking group called shadytel was able to legally stream from a satellite in geostationary orbit (just before reaching its EOL back in 2020):
Here, Karl Koscher (aka. supersat) goes in depth into how he and his team hacked the AnikF1R satellite and streamed footage from space.
Note: The whole presentation can be pretty much summarized in this quote taken from a VICE article about this hack:
“Satellites basically just reflect whatever signal is sent up to them. There’s no authentication or anything,” he said. “If you’re loud enough, and if there’s another user on that transponder, you have to shout louder than them. But if there’s no one there, [the satellite] will just repeat it.”
And at this point I went down a rabbit hole of broadcast hacking and different events where someone or some group took over access of some satellite or broadcast network like the terrestrial relay attacks that happened back in the 1980s, the most infamous being Captain Midnight broadcast signal intrusion or the Max Headroom signal hijacking..
And if you wish to learn more about space jamming and satellite signal hijacking you can watch James Pavur‘s presentation on it from DEF CON:

(And this blog is getting a bit too long hence I decided to just get it over with so I can publish it already…)
Hacking & Resurrecting Zombie Satellites

(Footage taken from Death Stranding)
This part is an homage to the recovery of BEESAT-1 (Berlin Experimental and Educational Satellite 1):
What happens when a satellite is no longer needed?
One of two things rly:
It gravitates back to earth, suffers from orbital decay and burns to ashes in its atmosphere..
It somehow keeps orbiting earth indefinitely and finds that sweet spot where It can just keep rotating forever and becomes what’s called space debris…
And we can’t even communicate with it because nearly all 6 people who really knew how the satellite worked have probably retired and are either living by cabin in the woods or raising animals in a barn/smallfarm…
Here, It’s called a zombie satellite.
And honestly there is no general rule as to how you’d communicate with these satellites since each one is different, but there was a case where a hacker by the pseudonym @pistonminer was able to bring back a satellite from the dead and fix the telemetry.
The talk was presented at CCC (Chaos Communication Congress) and you can find the briefing and other interesting talks online.
(mirror can be found @media.ccc.de and the deutsche version of this talk is available on YT)
I won’t really go into the technical part of this whole talk because to me
It’s less hacking and more “How to deal with technical debt in space”…
I mean, herrgott nochmal, the camera wasn't even tested until It was launched into space!!
Anyways, the whole talk is more or less great if not for the constant tingling sound of the jingling collar…
And I appluad the persistence to be able to reverse and analyse archaic software.
Learn by hacking satellites yourself:
Simulation, Digital Twins & HACK-A-SAT!
HACK-A-SAT
I wanted to leave this part specifically for Hack-A-SAT as they are extremely underrated and udnerappreciated…
Seriously, their CTFs are some of the best content you can experience, from creative challenges to full on VR experience that barely more than a few hundred people got to experience…
I mean last year, Hack-A-Sat 4 made history as the world’s first CTF competition IN SPACE!!
And teams had control of different ground stations from the south pole where they’d compete over pwn’ing the space satellite!
and you can find a lot of cool content on their github (deptofdefense/hack-a-sat-library)

Open Source Software & Hardware for satellites
If you want to replicate a satellite and try to find various security vulnerabilities, you can try using UPSat as a frame of reference and maybe try and go from there…
It’s was the first satellite launched into orbit made entirely of open-source software and open-source hardware
Although I didn’t dig deeper into it here since It’s kind of outdated in today’s standards and unless you can fund launching your satellite into orbit, It’s basically either just a virtual satellite or just another rasberry Pi…
Gitlab link for the UPSat open source software+hardware
And you can check the authors’ video about it, they even dig deeper into the various challenges that come with:
There’s also the Open Source Satellite programme and they offer a free and open source version of their OBC (On Board Computer) just a year after the launch of the OSSat: Github Link for the OSSAT OBC
Various relevant links:
How “Digital Twins” Could Help Us Predict the Future | Karen Willcox | TED
DEF CON 30 - Hunting for Spacecraft Zero Days using Digital Twins
DEF CON 29 Aerospace Village - Hack A Sat 2 - The Good, the Bad and the Cyber Secure
Resources & References:
Section 0: (Influence & People)
I’m a firm believer that documenting the facts and knowledge should be associated with those who allowed us to get there… especially in cyber.
It is people, human beings, who are behind these black mirrors.
And this work could not have been done without standing on the shoulders of these giants!
I should also preface that the order has no indication of technical expertise or overall contribution and is solely based on personal preferance!!!
These people inspired me the most:
Andrzej Olchawa:
X: @0x4ndy
Site: https://andy.codes/
Seriously, this guy’s work opened my eyes to satellites-hacking and deserves the utmost respect o7!
He also has research on other hardware related stuff like HID attacks (this one being my favorite) and whatnot, so PLEASE CHECK HIM OUT!
How to crash a Spacecraft – DoS through Vulnerability in NASA CryptoLib v1.3.0
DEF CON 32 - Ground Control to Major Threat Hacking the Space Link Extension Protocol
Ground Control To Major Threat: Hacking The Space Link Extension Protocol - Andrzej Olchawa BSIDES
other stuff I seen/used/liked by him:
HID attack with Nethunter
Lennert Wouters
If you’re doing research on satellite security recently, chances are you’re gonna stumble upon this guy at least a few times:
@LennertWo
He’s a great Researcher who’s very famous for his SpaceX Starlink’s hack and presentation at DEF CON 30:
DEF CON 30 - Lennert Wouters - A Black-Box Security Evaluation of SpaceX Starlink User Terminal
which also has other variations where he also goes in depth:
Glitched on Earth by Humans: A Black-Box Security Evaluation of the SpaceX Starlink User Terminal (Black Hat)
François Quiquet (Blogs & Articles)
You can find various blogs and articles covering space related cybersecurity
“An analysis of the Viasat cyber attack with the MITRE ATT&CK® framework”
and the updated blog on dec 2023:
Viasat Attack: A Space Cyber Attack Post Mortem Investigation
Oh and by the way, he does also have a few French blogs here and there if you’re into that (some of which are about nature and adventure ˚˖𓍢ִ໋🍃˚.⛰️⋆☁️)
Angelina Tsuboi (Presentations, Courses and QnA’s):
website: https://www.angelinatsuboi.net/
github: ANG13T
@AngelinaTsuboi
Even though her name requires no introduction in the US, I have somehow only heard of her when doing this research on satellites 🙃
And her work has been a great influence since then towards me actually writing this!
DEF CON 32 - How I Developed a Low Cost Raspberry Pi Based Device for ADS B Spoof - Angelina Tsuboi
Thirsty Thursdays Live Show With Angelina Tsuboi - Focusing Aerospace Cybersecurity
Live Hacking QnA w/ Kody Kinzie
feel free to also check her udemy course on satellite security
Johannes Willbold
@jwillbold
Github
linkedIn
site: jwillbold.com
Space Odyssey: An Experimental Software Security Analysis of Satellites
Robin Bisping
Github
Site: www.robinbisping.ch
Relevant links:
ACM_digital_lib_profile
VSAsTer: Uncovering Inherent Security Issues in Current VSAT System Practices
Space Odyssey: An Experimental Software Security Analysis of Satellites
Vincent Lenders
@VLenders
linkedIn
Space Odyssey: An Experimental Software Security Analysis of Satellites
Site: lenders.ch
“Occupy Theweb” (audio talk & books)
A great hacker who goes by the pseudonym “Occupy Theweb”, famous for his books like “Linux Basics for Hackers” which you’ve probably read somewhere…
Also founder of “HACKERS ARISE” (https://www.hackers-arise.com/)
where you can find blogs specifically tailored for satellite hacking:
https://www.hackers-arise.com/blog/categories/satellite-hacking
The site also has articles about radios and critical infrastructure like:
https://www.hackers-arise.com/blog/categories/scada
https://www.hackers-arise.com/blog/categories/sdr-for-hackers
And if you want something to listen to, feel free to check this video by him & David Bombal:
“Satellite hacking (with real world example)
It covers orbital jamming and the Viasat hack etc…
Gerard de Jong
Loved his talk and thought I’d mention his socials
Karl Koscher
@supersat
Github
and you can find more about him here
Great Hacker!!!
And honestly his works are quite technical and very advanced for me x)
but again, famous for his DEF CON 30 Talk - Hack the Hemisphere
He also has a few more interesting talks like:
DEF CON 21 - Karl Koscher and Eric Butler - The Secret Life of SIM Cards
DEF CON 23 - Packet Capture Village - Karl Koscher - Sniffing SCADA
Karl Koscher: What I Learned Trying to Hack a 737
Clémence Poirier
Hacking the Cosmos: Cyber operations against the space sector: A case study from the war in Ukraine
Lessons from the Viasat cybersecurity attack. - N2K Networks (audio)
(mirror link at space[.]n2k[.]com )
Trawling Hacker Forums Uncovers Crucial Information on Space Cyber Attacks
What Does Selling Your Ground Stations Mean for Cybersecurity?
Jacob Oakley
Day 3, 1 PM - (Aerospace Village) Hacking Satellites: Houston, We Have a Problem, Jacob Oakley
Cybersecurity for Space: Protecting the Final Frontier - First Edition (ISBN-13:978-1484257319)
James Pavur
linkedIn
Google Scholar
Bio Page
Matteo Calabrese
linkedIn
ResearchGate
Google Scholar
Brandon Bailey
DEF CON 29 Aerospace Village - Brandon Bailey - Unboxing the Spacecraft Software BlackBox Hunting
DEF CON 28 Safe Mode Aerospace Village - Brandon Bailey - Exploiting Spacecraft
and in the case the link goes down there is a reupload at the aerospace village YT channel called:
DEF CON 28 Aerospace Village: Exploiting Spacecraft
CYSAT 2023: Demo “Hacking Spacecraft using Space Attack Research and Tactic Analysis”
Martin Strohmeier
Bio
linkedIn
Google Scholar
Oxford’s reference page & Biography
Interesting Talks:
DEF CON 32 - Analyzing the Security of Satellite Based Air Traffic Control - Martin Strohmeier
DEF CON 32 - Exploiting Bluetooth from your car to the bank account$$ - Yso & Martin Strohmeier
Aerospace Village: Day 2, 130 PM - Elon, Twitter and the PIA: How not to achieve privacy in aviation, Martin Strohmeier
and
Day 2, 2 PM-Labs & Trust: How to build a successful aviation cybersec research | Martin Strohmeier
Space Odyssey: An Experimental Software Security Analysis of Satellites
Ólafur Waage
@olafurw
Github
linkedIn
YT_channel
site: olafurw.com/
Honestly gained my respect for running DOOM on a satellite:
Running DOOM on a satellite
DOOM in Space - NDC TechTown
Github link of the ops-sat DOOM project (github/olafurw/opssat-doom)
Georges Labrèche
@georgeslabreche
Google_Scholar
linkedIn
Research_Gate
site: georges.fyi
Engineers AI&ML systems on-board satellites.
Check the papers he contributed to!! <3
Oleg Kutkov
@olegkutkov
site: olegkutkov.me
You can find pretty much everything Starlink/firmware/embedded systems related in his blogs:
Analysis and reverse-engineering of the original Starlink router
Initial analysis of the Starlink router gen2
Starlink rev 3 (V2) power architecture
Section_1: Interesting Research & Academic Papers
Now, satellite-hacking research has been quite a niche thing… but I’ve found a lot of research, even ones dating back to 2009! (Black Hat DC 2009 - Adam Laurie - Satellite Hacking for Fun and Profit)
I might also put stuff not relevant to space hacking and more like car/airplace hacking here like Jmaxxz - Your Car is My Car - DEF CON 27 Conference and Radio Hacking: Cars, Hardware, and more! - Samy Kamkar - AppSec California 2016
Aerospace Village
And here I decided to put relevant or interesting stuff that has to do with satellites in particular and embedded systems and IoT in general:
DEF CON 30 - Gal Zror - Hacking ISPs with Point-to-Pwn Protocol over Ethernet (PPPoE)
Aerospace Village YT videos and relevant twitter/X account @SecureAerospace
Note: It’s quite surprising how most of their vids barely reach a thousand views considering they do pentesting on planes like pentesting the Boeing 737NG airplane by Alexander Dodd or “Hunting for Spacecraft Zero Days using Digital Twins” by Brandon Bailey… Actually, the only popular video on this channel I found was because the Boeing 747s received critical sofware update via 3.5” floppy disks which is showcased in their video at 7:48 called DEF CON 28 Aerospace Village: 747-400 Walk through From a Hacker’s Perspective…
And honestly I get it.. some of the videos might be not interesting…
But I’m the kind of person who likes to listen to hackers just talking about the aerospace sector for fun… so I don’t know if I should be taken as a frame of reference x)
other interesting videos:
Building the Ultimate Budget Friendly Low Earth Orbit Satellite Ground Station
Interesting Research Papers
I’d usually post Sci-Hub links here…
but thought I’d just put the official links for relevant articles here
and leave the reader free to sail the high seas 🏴☠️
ADS-C Technical aspects and C Technical aspects and Implementation Status
Section_2: whoami
Now, I’m already used to IoT-device hacking; as in proficient when It comes to reversing firmware, exploiting binaries and scrolling through thousands of pages of datasheets… as for the astronomy and “science” part, I still have PTSD from Fourier Integrals and Maxwell’s equations…
So yeah…

but in no ways I’m a veteran expert when It comes to this stuff..
(I mean I’m still looking for an end-of-studies internship for heaven’s sake 🙃)
Which is why I decided to place my references at the bottom here just to reflect that…
Overall, I found this blog very entertaining to write… as in I learned new stuff and got to put my thoughts on a “permanent” medium (aka. the internet)…
So that’s cool…
And if you have any questions/remarks feel free to contact me (@sifu0nulls)
or email me at: saif.sebai.ensi@gmail.com
Now I can finally go back to playing Starsector or Factorio…